User Management
User Management is where users are added to the system, authorization groups are managed, user sessions can be reviewed, and external authentication integration can be configured.
User accounts can be authenticated locally or LiveNX can integrate with external user repositories for user authentication. Today, LiveNX supports the following external authentication methods:
• LDAP
• RADIUS
• TACACS+
• SSO
Please review this chapter for configuring LiveNX to these external repositories.
All user account authorization is done in LiveNX via Groups.
The User Management tab is where users are added to the system and managed.
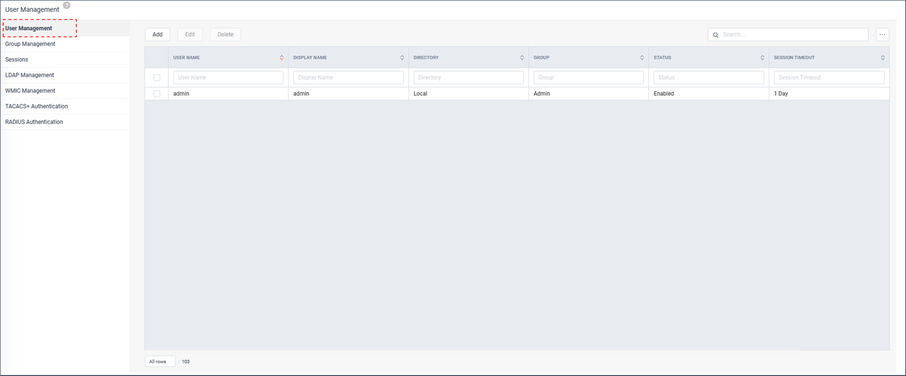
To add a new user, click .
The Add New User modal appears.
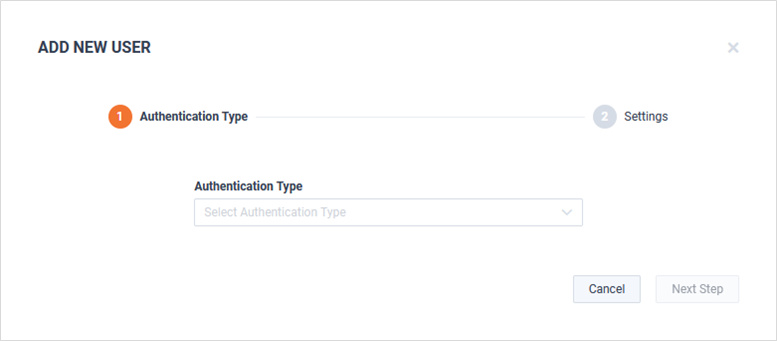
Select the Authentication Type and click .
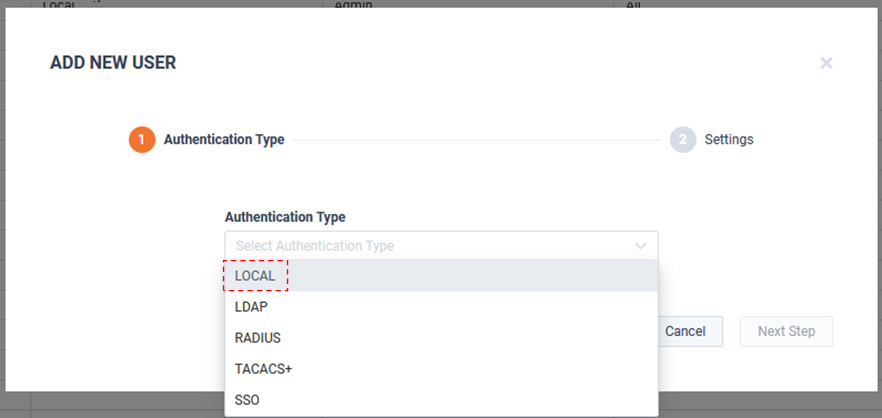
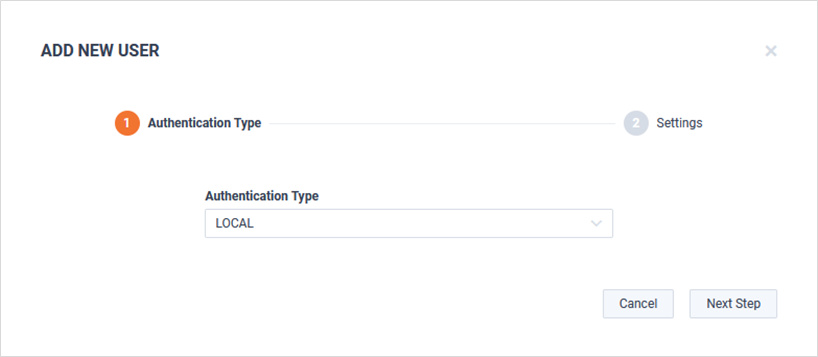
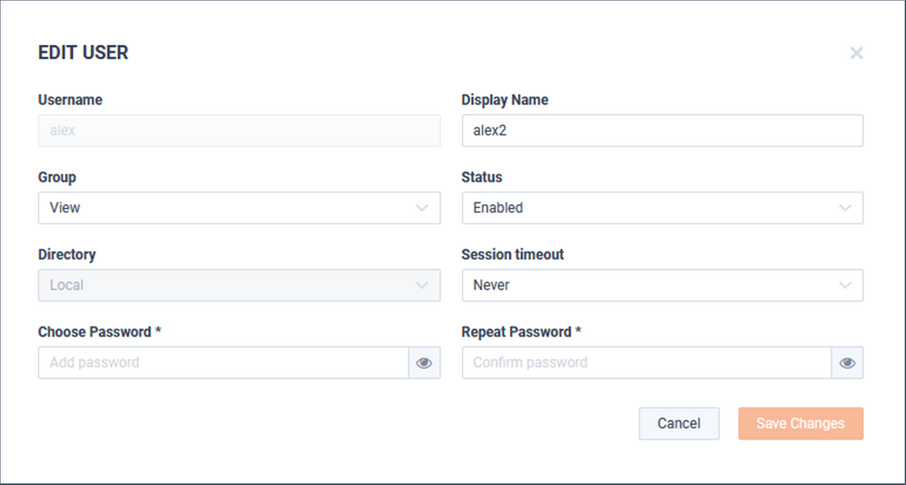
Define the user:
• Username
• Display Name
• Group
• Session Timeout
• Choose a password
• Repeat Password
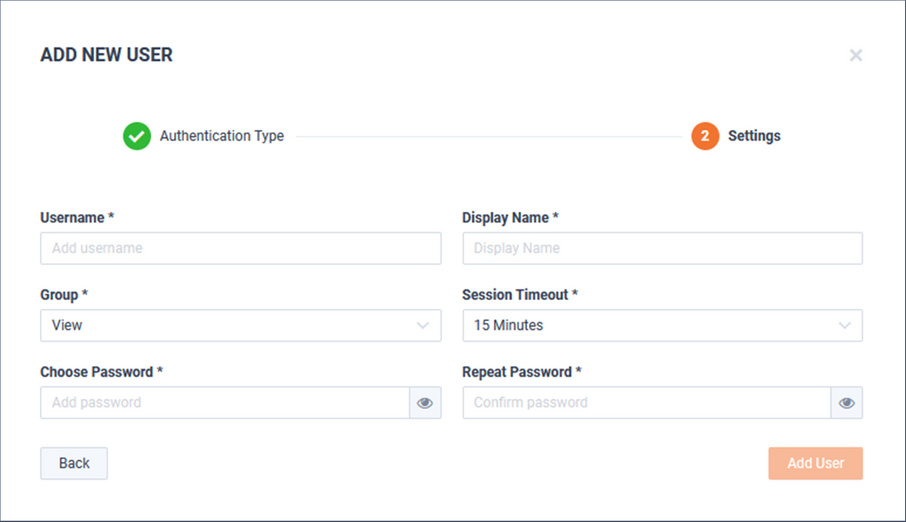
When finished, click .
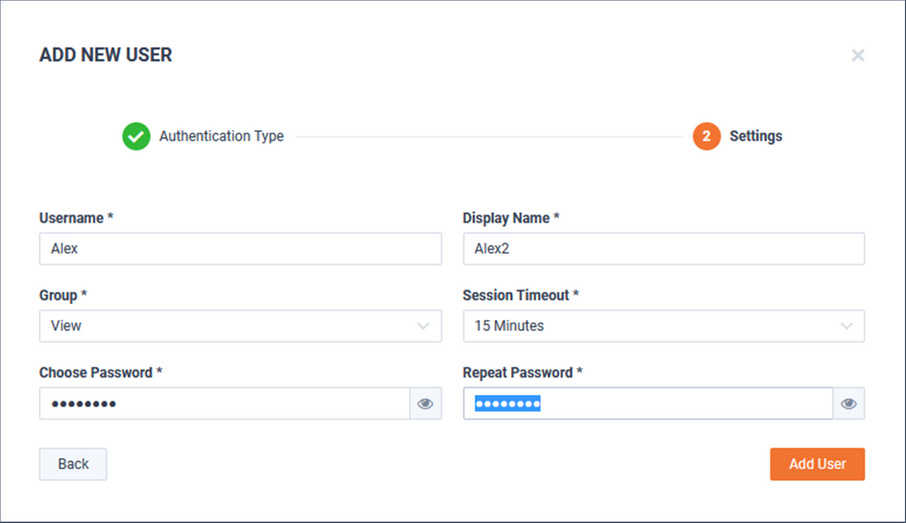
The new user will now be listed on the User Management tab.
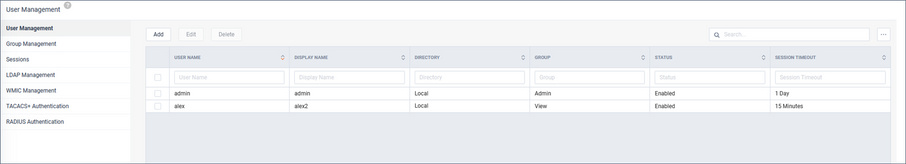
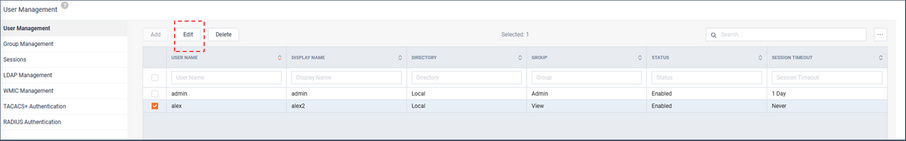
To edit the user, select the user and click .
All user account authorization is done in LiveNX via Groups. The Group Management tab is where Groups are added and managed.
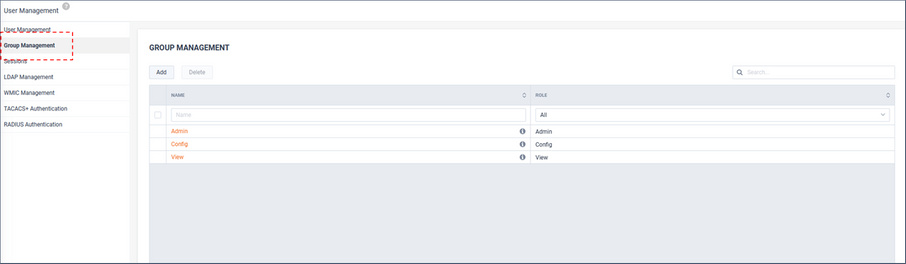
Authentication Groups have four components:
• Role – Defines the authorized capabilities of the group members, i.e., monitor only vs. config changes
• Device Authorization – defines which devices are visible for monitoring by group members
• Page Access – defines which pages are available in the Operations Dashboard (WebUI) for group members
• Users – which LiveNX users are a member of the group
Role
The group’s Role defines the authorized capabilities for the members of the group.
There are three Roles available: Admin, Config, and View. There capabilities will be summarized in the table below:
New Role | Description | Device Access | Capabilities |
|---|---|---|---|
Admin | Can perform any action for all resources. Is capable of making changes to the system that impact other users | All devices | All capabilities |
Config | Can perform any action for its selected resources. Is capable of making changes to the system that impact other users but at more limited level than admin. An example is that a “config” user will not be able to access “Settings” | Only devices for which a user has been given permission to access (All Devices by Default) | • In the Operations Dashboard: Config can optionally manage Devices, Custom Applications, Filters, Site • In the Engineering Console: Config can optionally control CLI GUIs (ie. Manage QoS, IP SLA, ACLs, PBR, etc.) |
View | Can primarily only monitor data for its selected resources. Is unable to make changes that impact other users. | Only devices for which a user has been given permission to access (All Devices by Default) | Monitor Only |
Device Authorization
Device Authorization defines which device’s SNMP and NetFlow metrics are visible by group members.
By default, all devices are available for all roles. Restricting visibility to selected devices can be accomplished by filtering devices, sites, or regions.
Page Access
• Operations Dashboard (WebUI) page access can be limited per role
• Most pages are accessible by all Roles.
• Some pages are accessible to only Admins.
• Some pages are accessible to Admins and Config.
The table below shows the pages only available to Admin and Config roles:
Section | Page | Required Page Access | Required Role |
|---|---|---|---|
Configure | Alert Managment | – | config/admin |
Configure | Application Management | Application Management | config/admin |
Configure | OID Polling | OID Polling | config/admin |
Configure | Device Management | Device Management | config/admin |
Configure | Filter Management | Filter Management | config/admin |
Configure | Site Management | Site Management | config/admin |
Gear Icon | Settings | – | admin |
Gear Icon | User Management | – | admin |
Gear Icon | LiveNX Server | – | admin |
Users
Defines which LiveNX users are a member of the group.